Amazon CloudFront is a Content Delivery Network (CDN) offered by Amazon Web Services (AWS). You can use CloudFront to deliver static and dynamic content, including images, videos, APIs, web applications, and other files, to end-users from a globally distributed network of edge locations. The Various Use Cases Amazon CloudFront If you use Amazon CloudFront, you […]
In today’s world of cloud computing, edge security and DDOS protection are crucial considerations for any organization with an online presence. Amazon Web Services (AWS) provides a range of tools and services that can help to protect against attacks and secure the edge of your infrastructure. What is Edge Security? Edge security refers to the […]
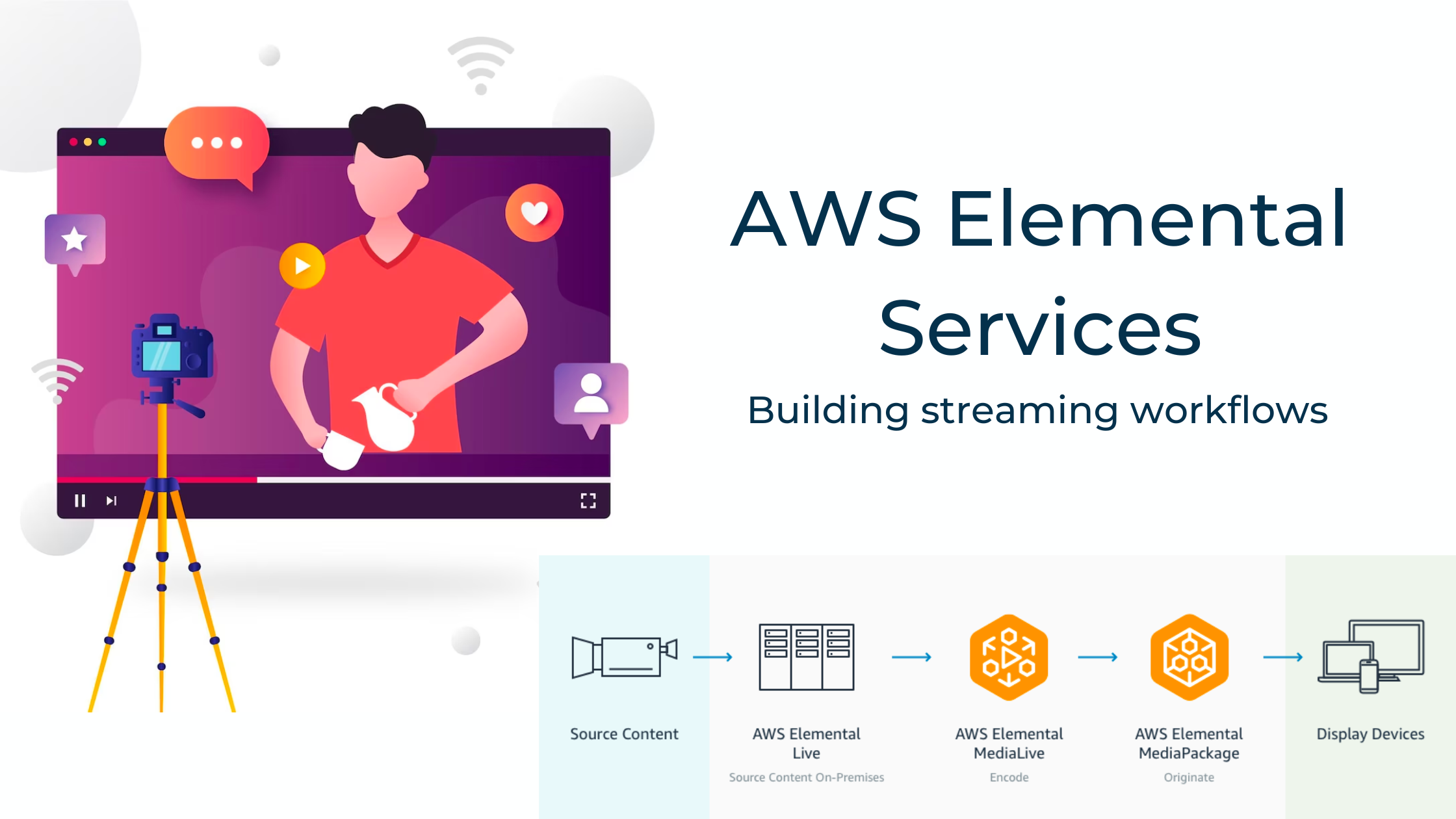
Live streaming requires consideration of various factors like ingesting, encoding, bandwidth and delivering a hassle-free playback experience. To deliver a smooth live streaming experience with AWS Cloud, you can use several services and tools to provide seamless content to a large audience. Live streaming workflows have many goals, like capturing durable messages, delivering them in […]
AWS WAF (Web Application Firewall) is a cloud-based web application firewall service that helps protect your web applications from factors and attacks that could affect the confidentiality, availability, and integrity of your web applications. With AWS WAF, you can create custom rules that block common attack patterns such as SQL injection, cross-site scripting (XSS), and […]